Test DirectAccess with a Windows 10 client
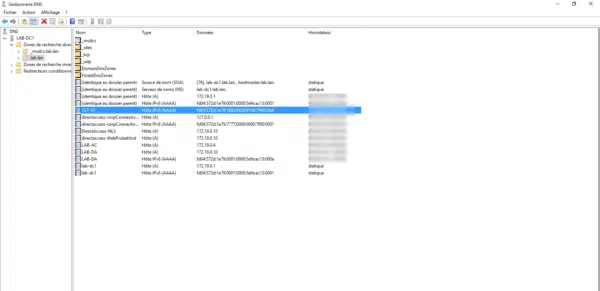
Before testing the configuration of a client computer, it must be connected to the corporate network, verify that the policy is applied using the command gpresult /r.
It is possible to verify the configuration before the following PowerShell command that returns the DirectAccess configuration:
Get-DAClientExperienceConfiguration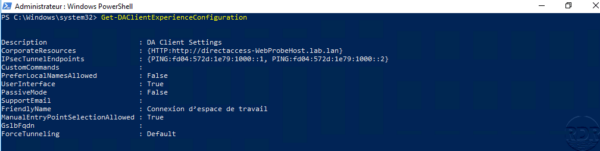
It is also possible to check the activation of DirectAccess in the Windows 10 connection settings with the addition of a DirectAccess section 1 .
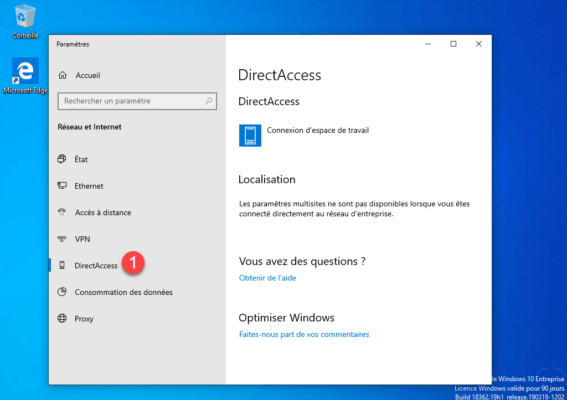
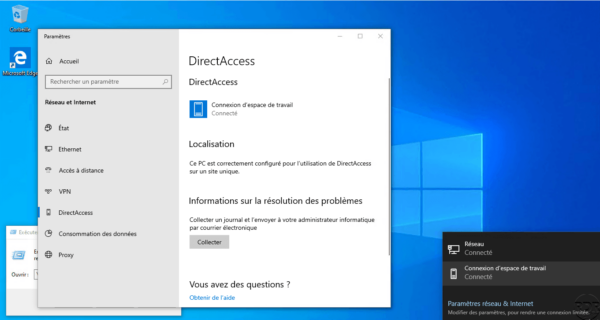
We can see on the screenshot above that we are located as being in the network of the company because the station can contact the probe.
If the DirectAccess section is unavailable, verify that the Network Connectivity Assistant (NcaSvc) service is started.
As a reminder, you must have an Enterprise version of Windows
Now place the computer outside the company network (Internet) and check that it connects …
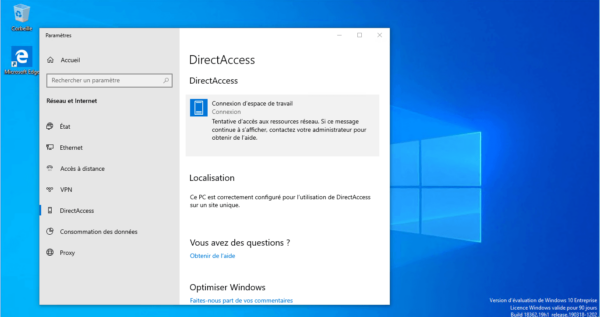
The computer is connected.
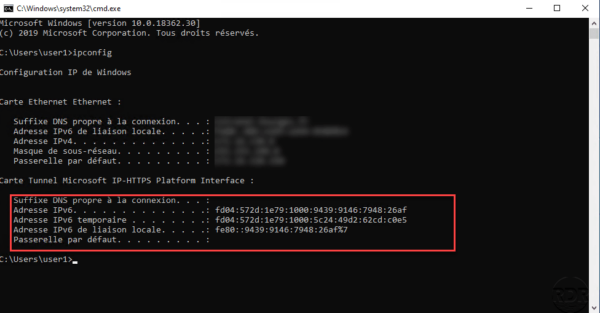
In a command window enter ipconfig to check the ipv6 address of the Microsoft IP-HTTPS Tunnel Card.
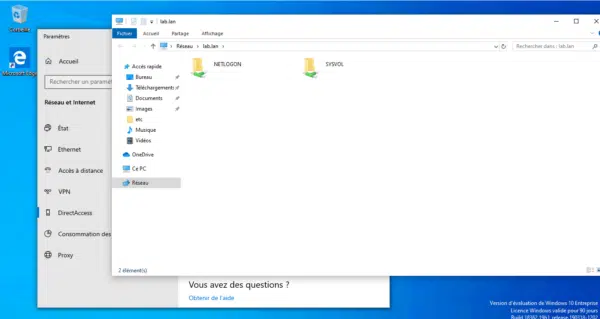
To validate the proper functioning, try to access a resource on the corporate network, in the screenshot below I access the domain controller by entering the Active Directory domain name.
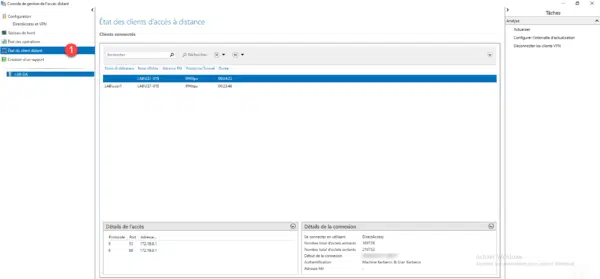
On the DirectAccess server on the Remote Access Management Console in Remote Client Status 1 , you can see the connected computer and user.
If we look at the DNS records on a domain controller, we find a record for the client connected with an IPv6.