General
Bitlocker : enable encryption with a TPM chip
Introduction In this tutorial, I will tell you how to activate Bitlocker with a TPM chip. Bitlocker is a feature of Windows that allows you to enable encryption of a hard drive in order to secure data. The TPM chip is a hardware chip which will store the decryption key and which is specific to …
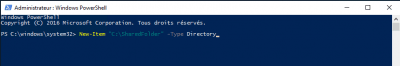
Create a folder in PowerShell
To create a folder in PowerShell, use the New-Item cmdlet indicating the location and name of the folder and set the itemType parameter with the value Directory to indicate that you want to create a folder.
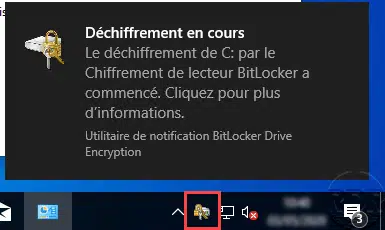
Disable Bitlocker on a drive
This “how to” tutorial explains how to disable Bitlocker on a hard drive.
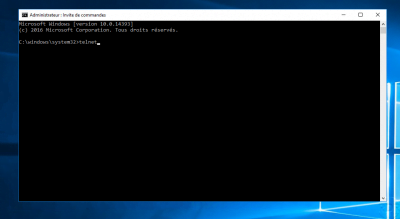
Use the Telnet client to test a network connection
Presentation In this tutorial, we will see how to use the Telnet client to test the connection to a service (IP: PORT) for diagnostic purposes. Telnet is a client / server TCP protocol that listens on port 23 which allows the administration of equipment (switches, firewall …) and of certain servers (UNIX, LINUX). It is …
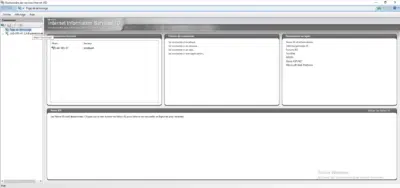
Windows Server : installation of the IIS role – Internet Information Services
In this tutorial, we will see how to install the Internet Information Services (IIS) role which allows you to install a Web server on Windows.
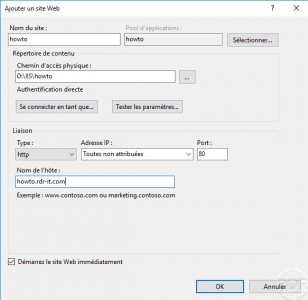
IIS – Add a site based on the DNS name
In order for the site to be available, it is necessary to create a record on the DNS server which manages the domain name.
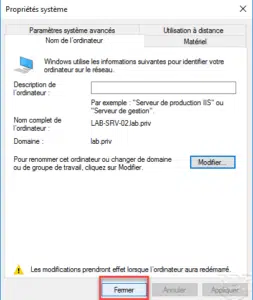
Windows Server : join an Active Directory domain
In this tutorial “how”, we will see how to join a Windows server with graphical interface to an Active Directory domain.
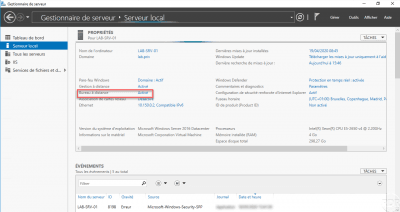
Windows Server : Enable Remote Desktop
This tutorial “how” explains how to activate the remote desktop on Windows Server with a graphical interface.
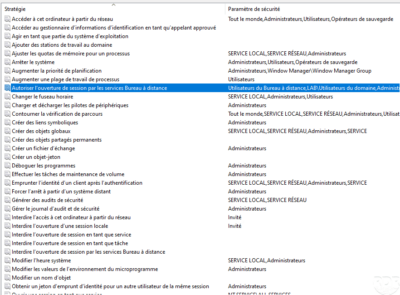
Remote desktop: configure who can connect
In this tutorial, we will see how to configure who can connect to the computer using Remote Desktop. This tutorial does not apply to RDS deployment, where this configuration is done at the collection level. This tutorial applies to computers and servers where the remote desktop is configured for takeover. There are several methods to …