Introduction
DirectAccess is a feature available with the Remote Access role, which allows you to set up an automatic connection solution to the corporate network for mobile computers or for small remote sites.
Unlike a VPN, the connection is initiated directly by a service on the remote computer, which allows for similar behavior if the workstation is in the corporate network:
- Applying group policies.
- Ability to open another user session in the Active Directory.
DirectAccess also has two other benefits that are:
- The automatic connection without manipulation on the part of the user.
- The ability to force internet traffic through the corporate network which allows to apply the rules of web filtering (proxy).
DirectAccess relies on the IPv6 protocol for communication between the corporate network and the customer.
Before establishing the connection, the client tests access to a probe to find out if it is in the company network or outside.
For DNS resolution, a Group Policy configures the NRPT table so that the computer when it is connected to the corporate network sends the requests from the local domain to the DirectAccess server.
It is possible to increase the security of connections by identifying computers with a certificate.
In this tutorial, we will see how to deploy DirectAccess with a server with a single network card behind a firewall.
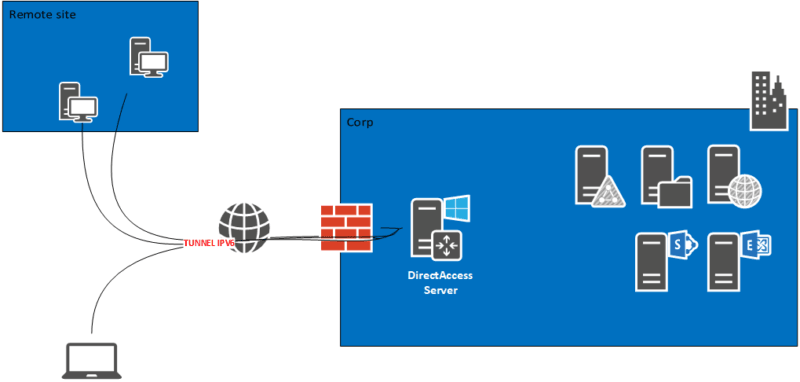
This tutorial can also be used to deploy DirectAccess with Windows 2012R2
To work you have to make the server accessible from the Internet by correctly configuring the NAT / PAT.
Documentation Microsoft : https://docs.microsoft.com/fr-fr/windows-server/remote/remote-access/directaccess/directaccess
Prerequisites
Deploying and using DirectAccess requires several prerequisites:
- Being in a replicated Active Directory environment with DFS-R
- Dedicated a server to this role:
- Member of the domain
- The Windows firewall must be activated, it is this one that manages the transition IPv4 <-> IPv6
- Dedicate an Active Directory group for computers that use DirectAccess.
- Customers who are members of the domain:
- Windows 7,8,8.1,10 Enterprise
- Firewall activated
If you want to enable post authentication with a certificate, you need to set up an enterprise CA.
So that users can retrieve the DirectAccess configuration, they must be configured in the enterprise network.
Ports and protocols used by DirectAccess
Here is the list of ports and protocol to open on a firewall to authorize Direct Access
Access in IPv4 :
- TCP 443: for clients using IP-HTTPS which allows the encapsulation of IPv6 packets.
- UDP 3544: for customers use Teredo technology.
- IP 41 protocol: for customers using 6to4 technology.
- TCP 62000: If the network location server is on the DirectAccess server itself and the DirectAccess server has only one network adapter.
Access in IPv6 :
- IP 50 protocol
- UDP 500