In this tutorial, I will walk you through how to disable a cipher suite also call cipher.
If you arrive on this tutorial by a search engine, there is a good chance that it is due to a vulnerability test and that you have an alert that goes up because vulnerable cryptographic suites (cipher) are active.
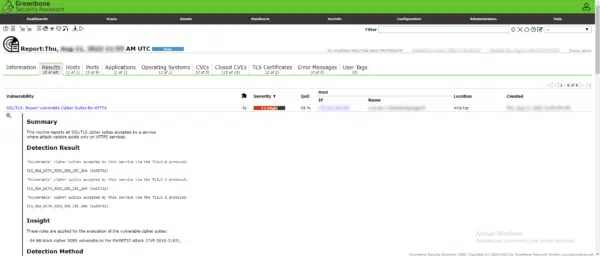
Here is an example of an alert you may have:
To illustrate this tutorial, I will explain how to disable the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher suite on Windows Server.
On the Windows server, open a PowerShell prompt as administrator. Before moving on to deactivation, we will see how to display the cipher suites with the cmdletGet-TlsCipherSuite.
Enter the command below to display the list:
Get-TlsCipherSuite | Format-Table Name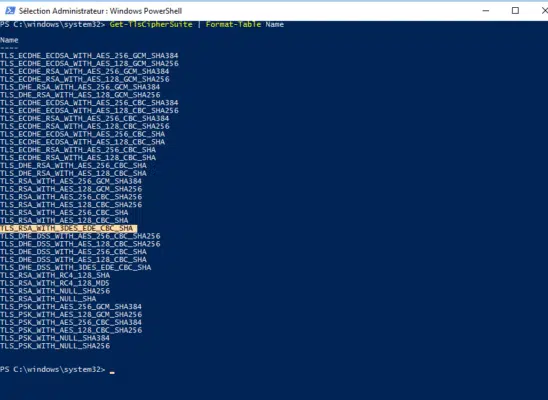
On the capture, we can see the active “ciphers” and we can clearly see the TLS_RSA_WITH_3DES_EDE_CBC_SHA suite that we want to deactivate.
To disable a cryptographic suite, we will use the cmdlet Disable-TlsCipherSuite indicating the name of the suite as a parameter.
Here our case, we will enter the command below:
Disable-TlsCipherSuite -Name "TLS_RSA_WITH_3DES_EDE_CBC_SHA"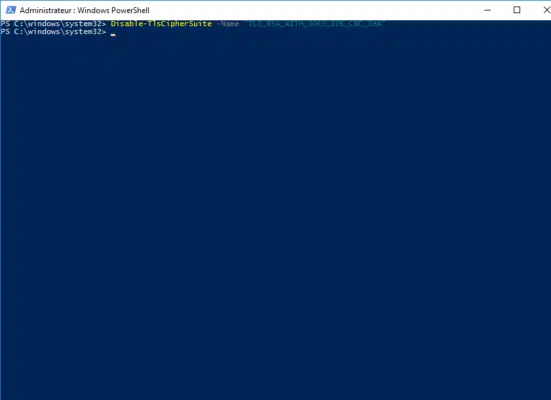
How can be seen on the capture, the cmdlet has no return.
To verify that the command has been placed, you can display the list of ciphers and verify that it is no longer in the list.
Get-TlsCipherSuite | Format-Table NameIf you use a tool like OpenVas, you can run a scan again and verify the vulnerability is no longer present.
On the capture below, after a new scan, we can see that an arrow indicates a drop in score.
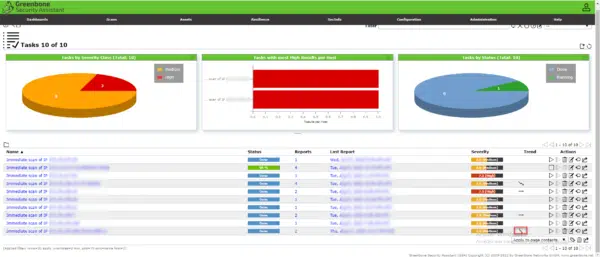
In the list, we can see that the vulnerability on the TLS_RSA_WITH_3DES_EDE_CBC_SHA suite is no longer present.
You now know how to deactivate a cryptographic suite (cipher) on Windows Server, it can easily be done on an entire Windows server park with Ansible and the PowerShell module.
Here is an example of using the PowerShell module in an Ansible playbook.



Although I disabled that Cipher Suite, OpenVas tells me it isn’t disabled. Am I doing something wrong? If I look them up they don’t show up anymore.
High (CVSS: 7.5)
NVT: SSL/TLS: Report Vulnerable Cipher Suites for HTTPS
Summary
This routine reports all SSL/TLS cipher suites accepted by a service where attack vectors exists
only on HTTPS services.
Vulnerability Detection Result
‘Vulnerable’ cipher suites accepted by this service via the TLSv1.0 protocol:
TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
‘Vulnerable’ cipher suites accepted by this service via the TLSv1.1 protocol:
TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
‘Vulnerable’ cipher suites accepted by this service via the TLSv1.2 protocol:
TLS_RSA_WITH_3DES_EDE_CBC_SHA (SWEET32)
Good morning,
On which service (http/rdp/…) is the certificate detected? On HTTPS if it is an Apache or Nginx server, you have to look at this one.
Romain