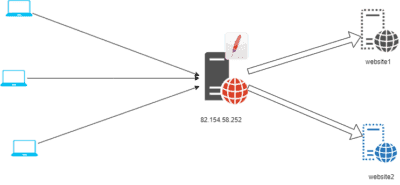
Active Directory: setting up a third-party system (tiering)
In this tutorial, I will explain how to configure a tiering system in an Active Directory environment, more specifically how to configure group policies (GPOs). This tutorial is not a complete guide to setting up tiering, but it does explain the basic GPOs you need to set up. This tutorial is not a complete guide …