Presentation
In this tutorial, we will see a feature built into Windows, folder and file access auditing.
This function allows logger access to resources (files and resources). It may be worthwhile to enable auditing on sensitive enterprise files to see if unauthorized people are trying to access it.
Audit configuration
Folder configuration
1. On the file server, open the Share Properties by the Server Manager, go to Permissions 1 and then click Customize Permissions 2 .
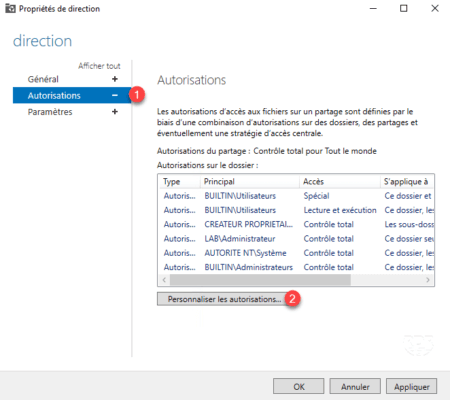
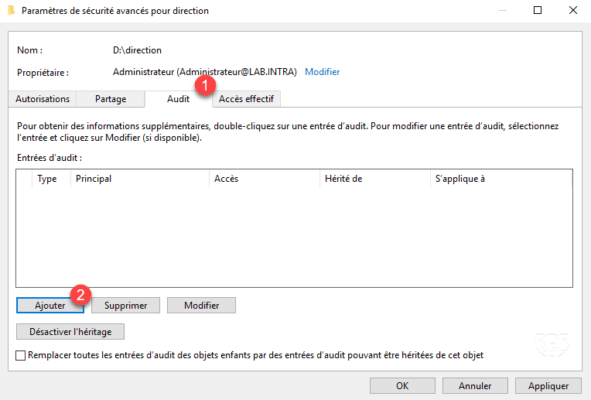
2. Go to the Audit tab 1 and click on Add 2 .
3. Select the users to be audited 1 , the type (Succeeded, Failed or All) 2 , check the items to be saved 3 and click OK 4 .
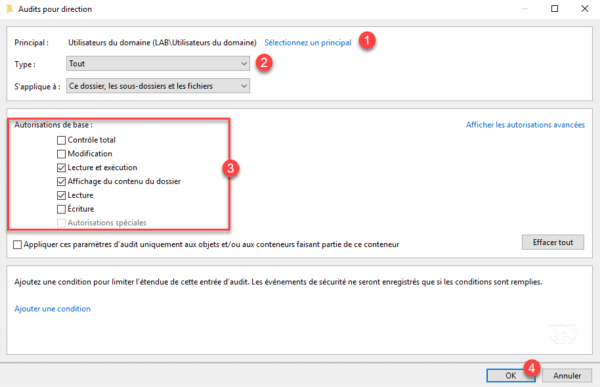
To view all available permissions, including deletes, click View advanced permissions.
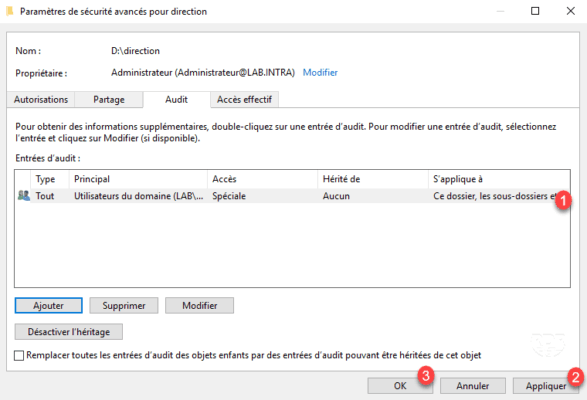
4. The audit is added 1 and visible how an authorization NTFS., Click on Apply 2 then OK 3 and close the properties window of the share.
Server configuration
To work it is necessary to activate the object access audit on the server.
1. Open an execute window (crtl+R) and enter gpedit.msc to access the local policy console of the computer.
2. Edit the Audit Object Access 1 setting located in the following location: Computer Configuration / Windows Settings / Security Settings / Local Policies / Audit Policy.
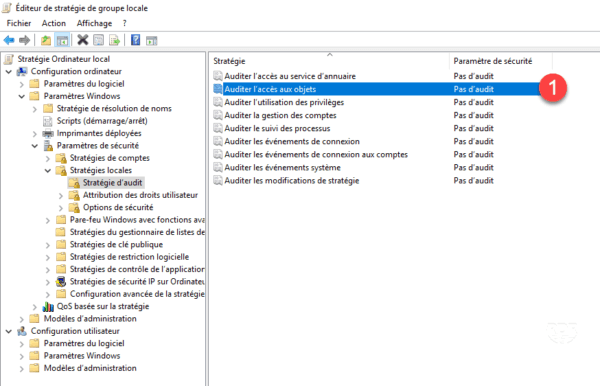
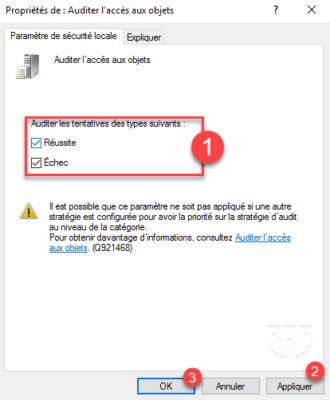
3. Configure the types of audit to activate 1 and click on Apply 2 then OK 3 .
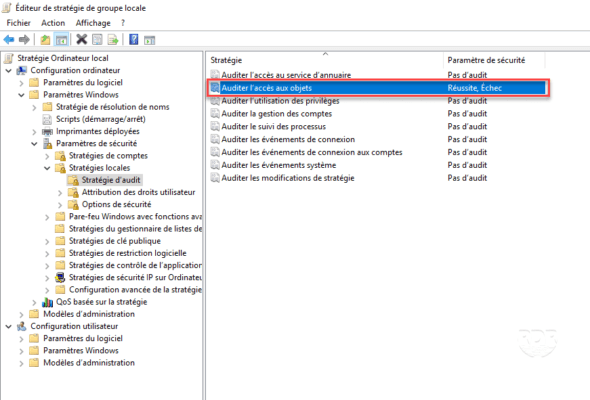
4. The policy is configured.
5. Force a policy update, by opening a command prompt as administrator and passing the gpupdate command.
View the logs
1. In order to generate logs, make access to folders and files according to the audit parameters.
2. On the server open the Event Viewer and go to Windows Logs 1 / Security 2 . Search for events in the File Systems category.
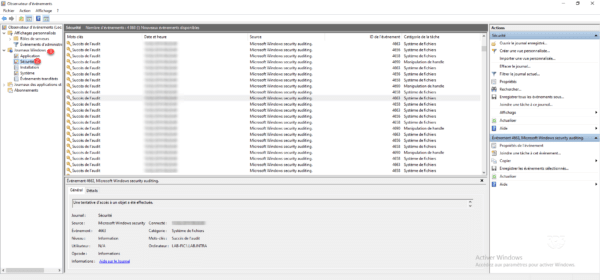
3. Example of logs:
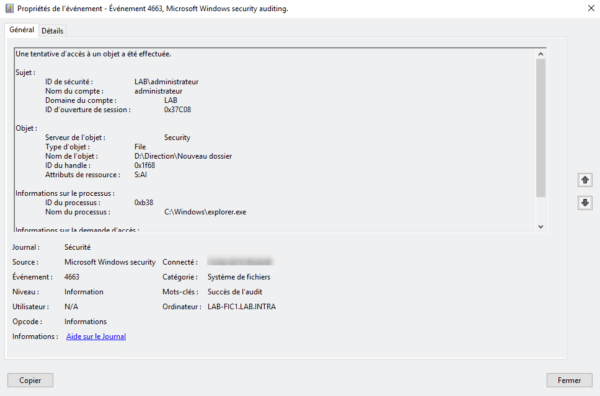
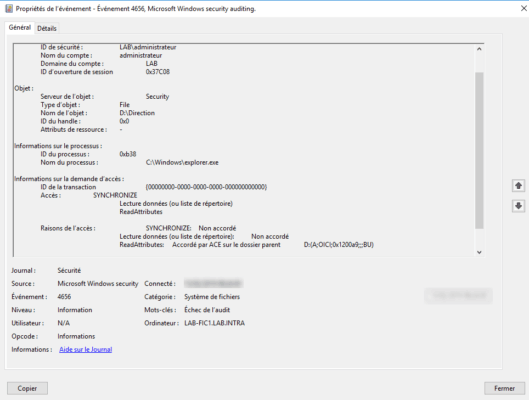
Conclusion
With auditing features, you can now record people who are roaming about shares and who are too curious.
Personally I advise you to activate this feature on sensitive folders and record only refusals, because the number of logs can quickly become important and also impact performance.
In order to better secure access to shares, I also recommend that you enable enumeration based on access.