Presentation of FSMO roles
In an Active Directory environment, there are 5 Flexible Single Master Operation (FSMO) roles, two roles are unique in the forest and the other three are unique in a domain.
A domain controller can have none or more FSMO roles.
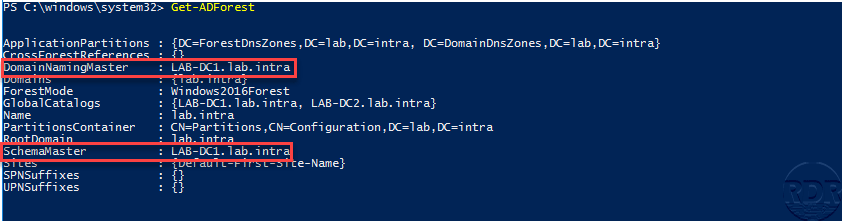
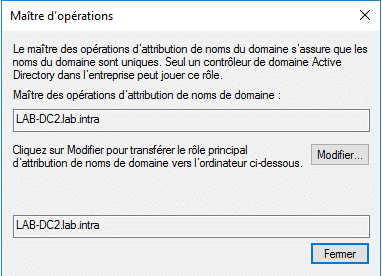
Domain Naming Master
It is unique in the forest, it is responsible for adding and removing domains in the forest.
Schema Master
It is unique in the forest, it manages the Active Directory schema which contains the set of objects that can be created and the attributes. He is the only one who can modify the diagram.
Example: when adding the Exchange service to your organization, it is this role which modifies the attributes during the preparation of the AD.
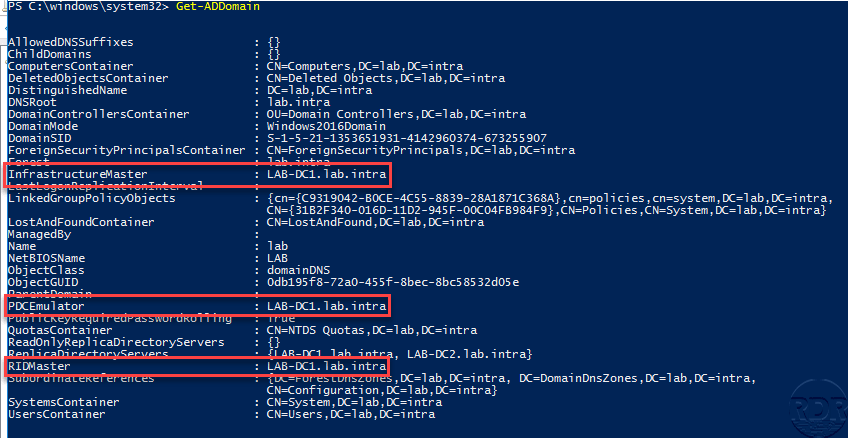
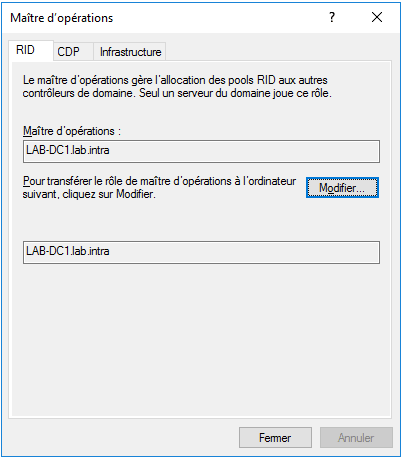
RID Master
It is unique within the domain, it distributes an RID pool to each domain controller to ensure that each SID delivered by a DC will be unique
Primary Domain Controller (PDC) Emulator
It is unique within the domain, it takes care of the synchronization of the time between the various servers and computers and the modification of passwords as well as the locks of accounts.
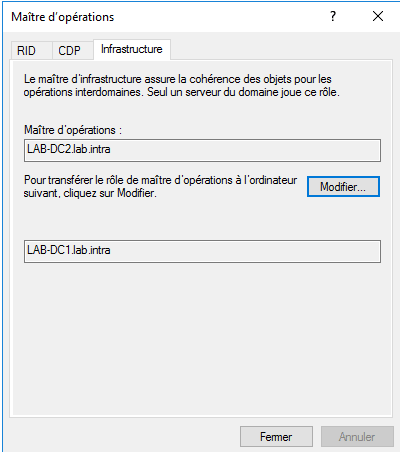
Infrastructure master
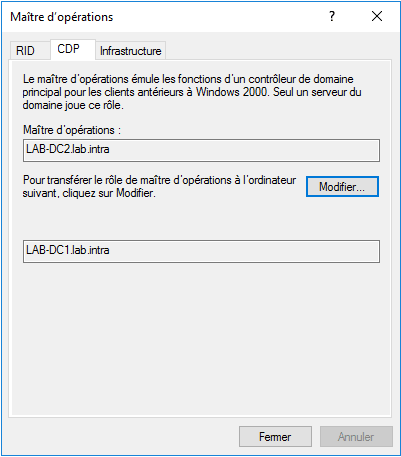
It is unique within the domain, its role is to manage inter-domain references.
Show FSMO
To display FSMO roles, several commands are available:
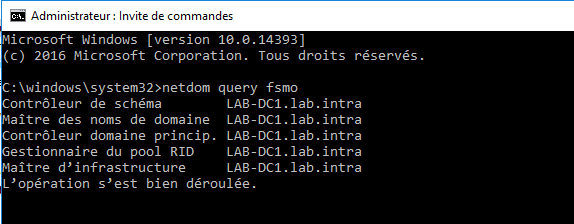
netdom query fsmo
In PowerShell, you must use the Get-ADForest and Get-ADDomain cmdlet.
From the consoles:
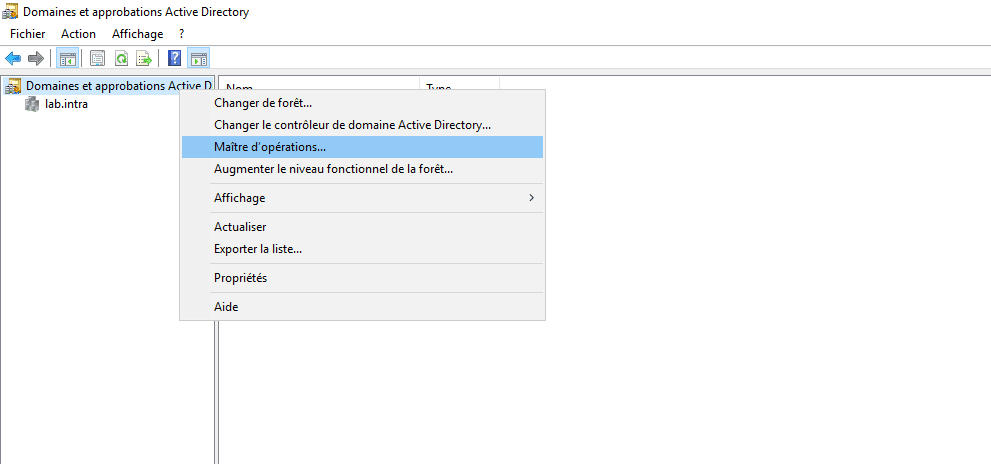
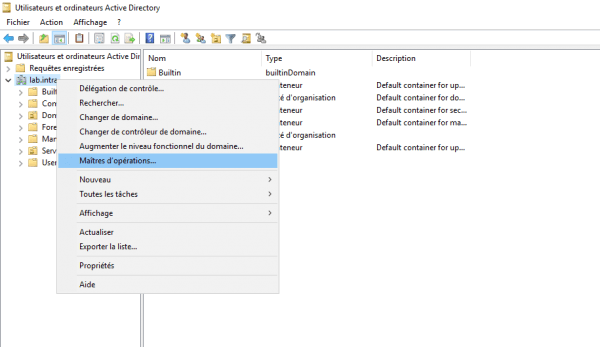
Open the Active Directory Users and Computer console to access the domain’s FSMO role, right-click on the domain and click on Operation masters.
The Domain and Active Directory Trust console provides access to the FSMO Operation Master role for naming. Right click on the console name and click on Operation Master.
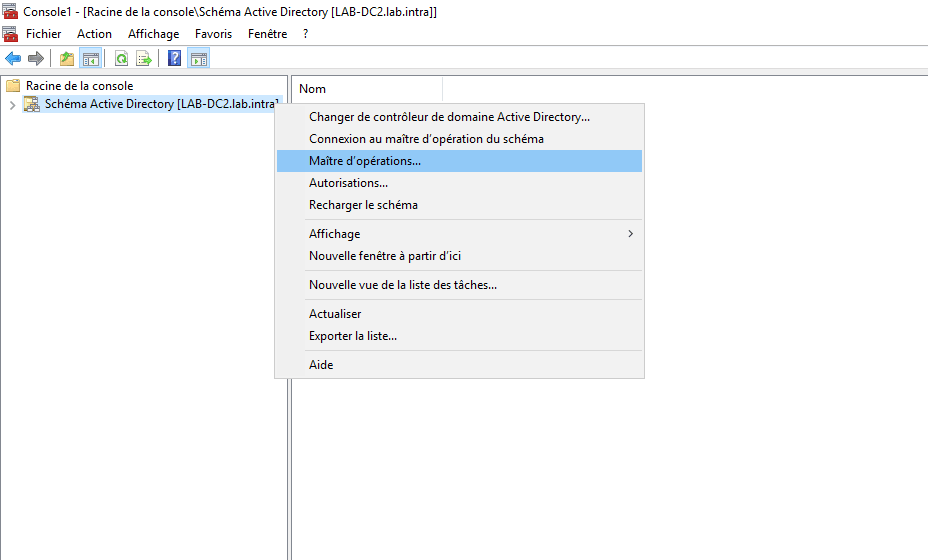
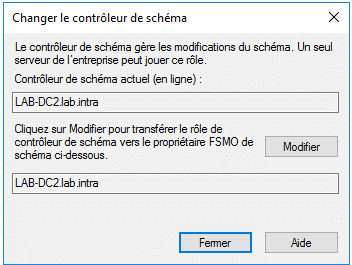
The Active Directory Schema console provides access to the Schema Master FSMO role. Right click on the name of the console and click on Operation Master.
The Active Directory Schema MMC is not available natively, it must be declared.
Transfer FSMO roles
For several reasons, you may need to transfer roles from one controller to another. There are two methods:
Normal: use this method preferably if you can, this requires that all the controllers are available.
Seize: use if you want to transfer a role from an offline controller.
The transfer can be carried out using the ntdsutil tool, in PowerShell with Move-ADDirectoryServerOperationMasterRole or using the various administration consoles.
For a forced transfer, it is not possible to do it by graphic consoles.
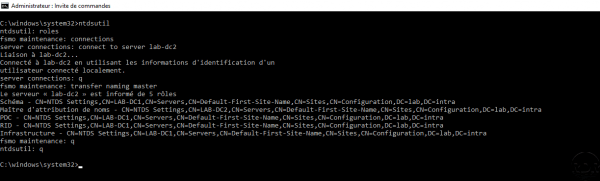
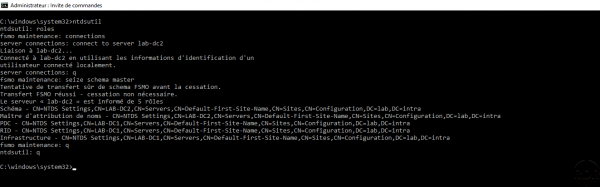
NTDSUTIL
Normal
Open a command window in “Administrator” mode and enter the following command:
ntdsutil
Enter FSMO roles maintenance mode:
roles
Enter the following commands to connect to the server that will receive the role (s):
connections connect to server nom_du_dc q
The commands to make the transfer (s):
# Maitre d'attribution transfer naming master # Contrôleur de schéma transfer schema master # Maitre RID transfer RID master # Emulateur PDC transfer pdc # Maitre infrastructure transfer infrastructure master
At each transfer request, you will have to confirm your action through a dialog box.
Exit ntdsutil by entering q.
Example of transfer:
Seize
Open a command window in “Administrator” mode and enter the following command:
ntdsutil
Enter FSMO roles maintenance mode:
roles
Enter the following commands to connect to the server that will receive the role (s):
connections connect to server nom_du_dc q
The commands to make the transfer (s):
# Maitre d'attribution seize naming master # Contrôleur de schéma seize schema master # Maitre RID seize RID master # Emulateur PDC seize pdc # Maitre infrastructure seize infrastructure master
At each transfer request, you will have to confirm your action through a dialog box.
Exit ntdsutil by entering q.
Example :
PowerShell: Move-ADDirectoryServerOperationMasterRole
The transfer in PowerShell is simpler, the same command allows to make the two types of transfer. It is also possible to transfer several roles in the same order.
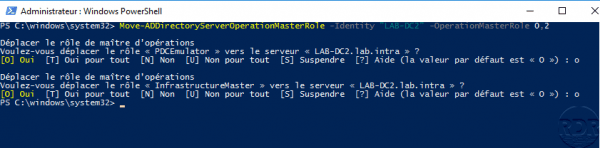
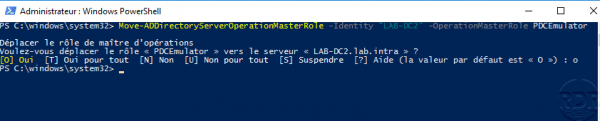
Example of normal transfer:
Move-ADDirectoryServerOperationMasterRole -Identity "LAB-DC2" -OperationMasterRole PDCEmulator
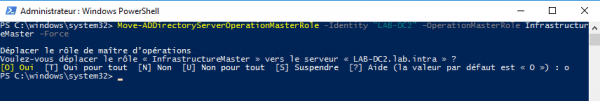
Example of seize :
Move-ADDirectoryServerOperationMasterRole -Identity "LAB-DC2" -OperationMasterRole InfrastructureMaster -Force
Example of transfer of several FSMO roles
Move-ADDirectoryServerOperationMasterRole -Identity "LAB-DC1" -OperationMasterRole PDCEmulator, InfrastructureMaster
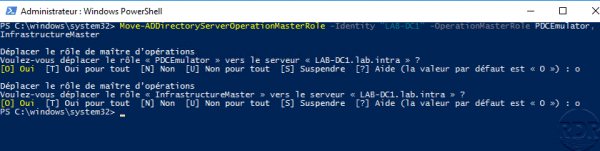
In value for the -OperationMasterRole parameter, it is possible to indicate a number which corresponds to the role.
| Identifiant | Rôle FSMO |
| 0 | PDC Emulator |
| 1 | RID master |
| 2 | Infrastructure master |
| 3 | Schema master |
| 4 | Domain naming master |
Example of transfer using the identifier:
Move-ADDirectoryServerOperationMasterRole -Identity "LAB-DC2" -OperationMasterRole 0,2