Presentation
The trust relationship between two Active Directory drill bits / domains is a trusted link that allows authenticated users to access resources in another domain.
An approval relationship may be:
- Unidirectional: access to resources is only available in one direction (A) -> (B).
- Bidirectional: access to resources is available in both directions (A) <-> (B).
- Transitive: If (A) and (B) have a transitive trust relationship, if (B) approves a domain (C) it will be approved in (A).
In which case an approval relationship is required:
- Setting up a child domain.
- Takeover / merger of business to allow resource access.
- SI segmentation (geography / service / …).
In this tutorial, we will see how to set up a trust relationship between two forests as if we had just acquired a company.

Prerequisites
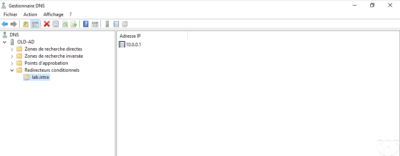
In order to be able to properly discuss the drills between them, it is necessary to set up a conditional forwarder on each DNS server.
Configure the trust relationship
The manipulations were performed on a domain controller on lab.intra.
Open the Active Directory Domain and Trust console, right-click on domain 1 and click Properties 2 .
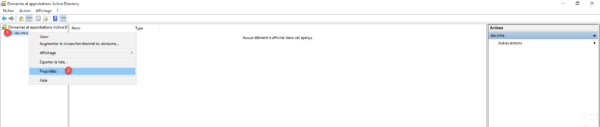
Go to the Approvals tab 1 and click on New approval 2 to launch the wizard.
When launching the wizard, click Next 1 .
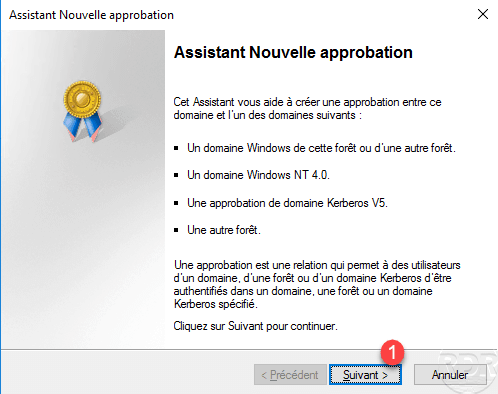
Indicate the domain 1 with which the trust relationship is made and click Next 2 .
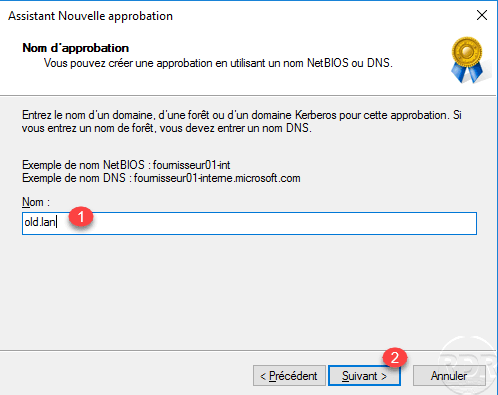
Choose Approval Type: Forest Approval 1 and click Next 2 .
Configure the direction of approval, in the example we will choose Bidirectional direction 1 and click Next 2 to validate.
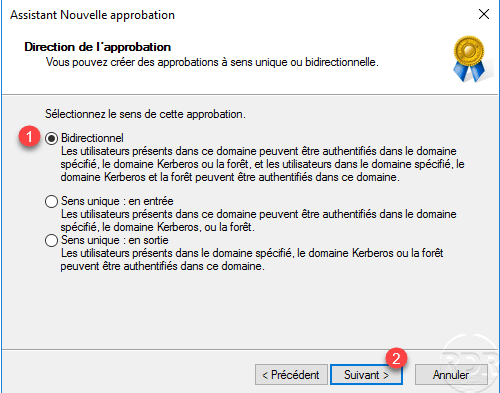
Choose the option This domain and the specified domain 1 , this allows to directly create the approval on the other domain. Click Next 1 .
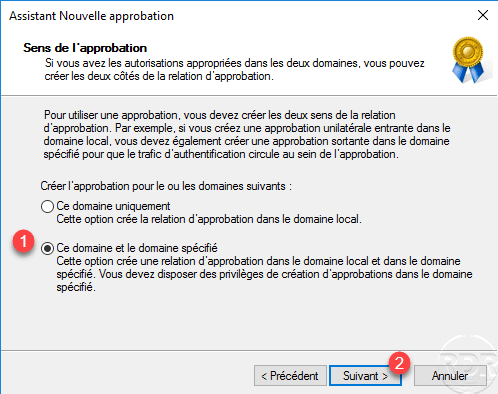
Enter the identifiers 1 of an Administration account in the specified domain then click Next 2 .
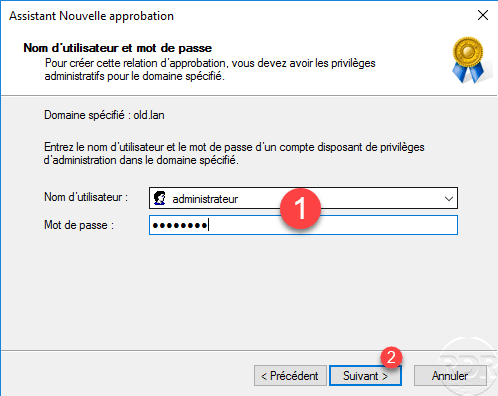
Choose the Authentication option for all forest resources 1 and click Next 2 .
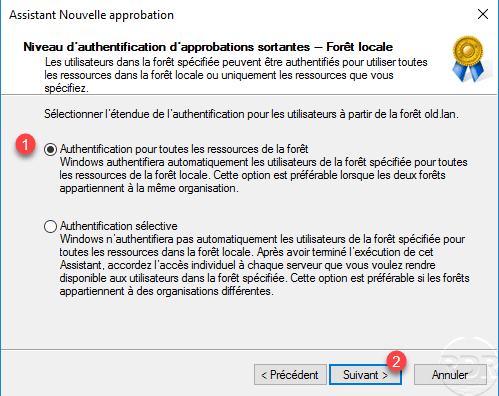
Authentication for all forest resources will allow users from both domains to log on to all available positions. If you want to set up a Selective Authentication, I invite you to read this article.
Also choose Authentication for all forest resources 1 for users from the local forest to the other forest and click Next 2 .
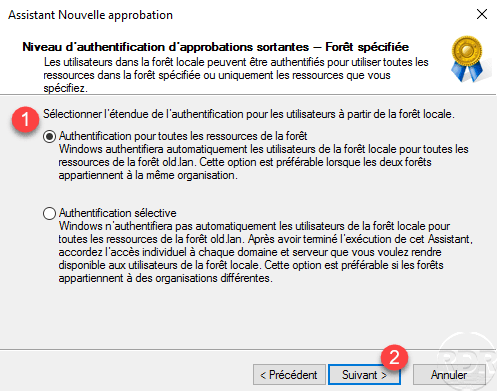
A summary of the trust relationship is displayed, click Next 1 to create the relationship.
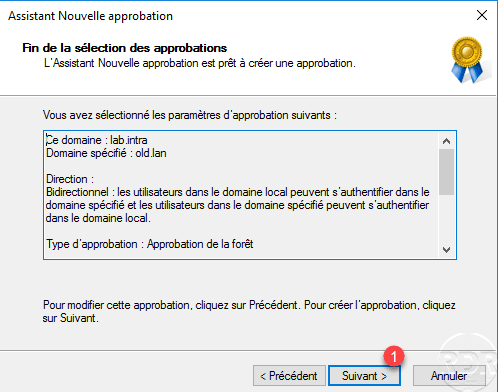
The trust relationship has been created, click Next 1 .
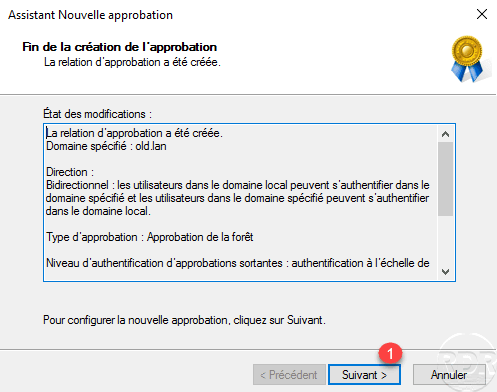
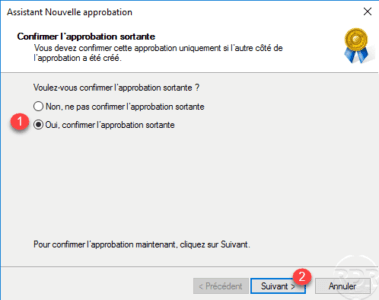
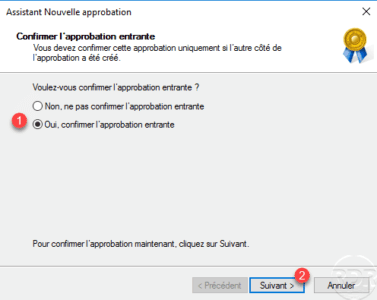
Confirm outgoing and next approval by selecting Yes 1 and clicking Next 2 .
Click Finish 1 to close the wizard.
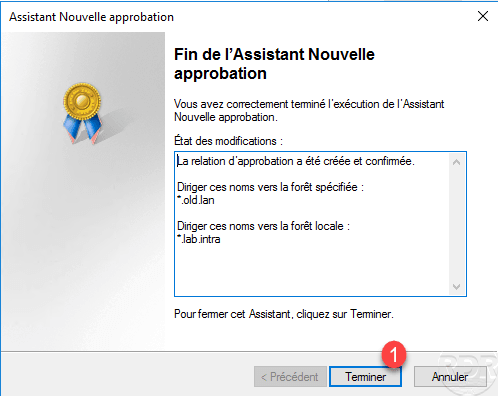
We see that the trust relationship has been created.
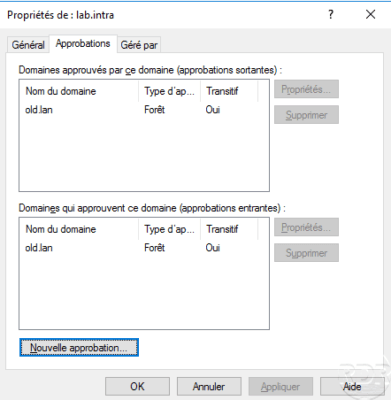
On a controller in the other forest, also verify that the relationship has been created.

Test the trust relationship
To validate the approval, we will do 2 tests:
- On a member post of the lab.intra domain, we will open a session with a user who is a member of the old.lan domain
- We will make a member of the domain lab.intra from a group of the domain old.lan
Log on to a post in another domain
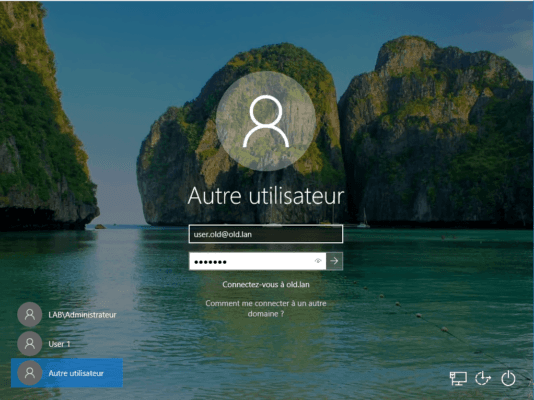
On a computer in the lan.intra domain, change the user and enter the credentials of a user from the old.lan domain by specifying his domain in the identifier.
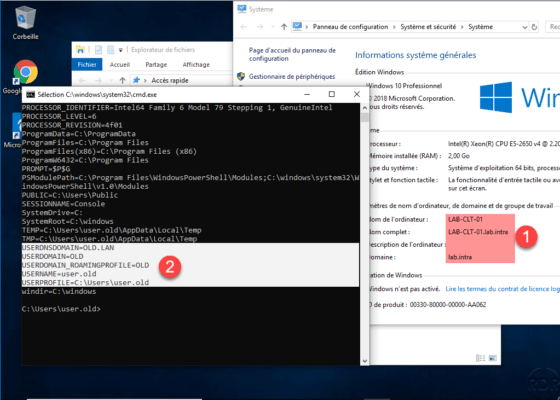
Once the session is open, launch a command prompt and enter SET, in the screenshot below we see that the computer is in the domain lab.intra 1 and that the user is a member of the old domain. lan.
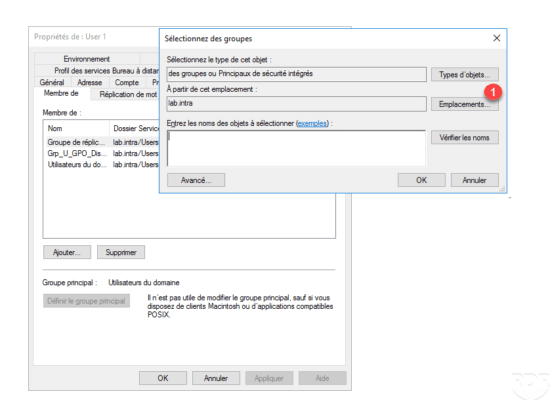
Join a group in the trusted domain
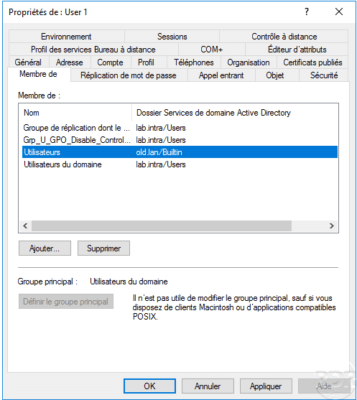
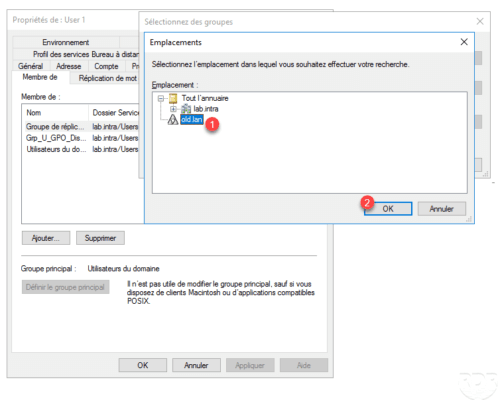
Go to the properties of a user in the lab.intra domain to add it to a group. In the group selection window, click Locations 1 .
Choose the approved domain 1 and click OK 2 .
Select a group 1 and click OK 2 to add it to it.
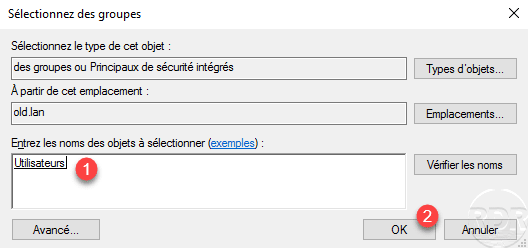
The user is now part of a group in the trusted domain.