Intro
In this tutorial, we will see how to prevent local logon on Windows servers.
What you should know is that by default all users are allowed to log on locally to Windows except for domain controllers.
For servers in Workgroup, the problem is less posed but for servers members of a domain, all users can open a local session provided they have physical access to the machine or by tools Teamviewer type.
Prevent local logon
In the tutorial, the manipulation is done locally, it is quite possible to do it by a group policy through the Active Directory.
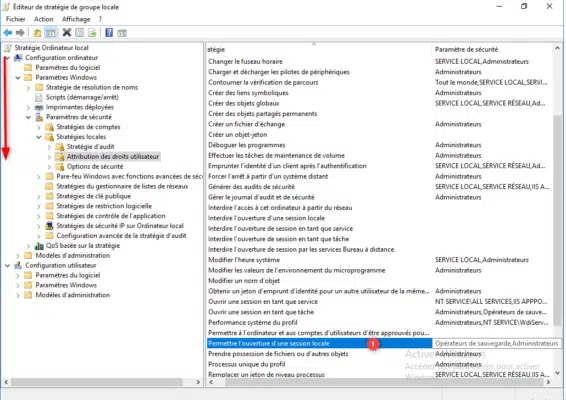
Open the Local Group Policy Editor console (gpedit.msc) and go to the Computer configuration / Windows settings / Security settings / Local policies / Allocation of user rights location. Double-click to open the Allow local session parameter 1.
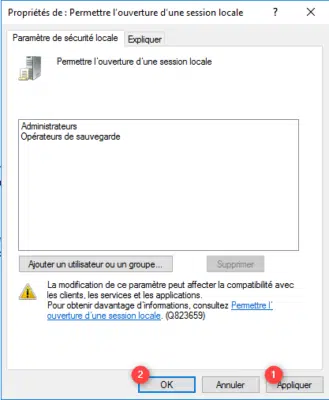
As you can see in the screenshot below, users have the authorization to open a local session (remote desktop sessions are not affected). Select Users 1 and click on the Delete 2 button.
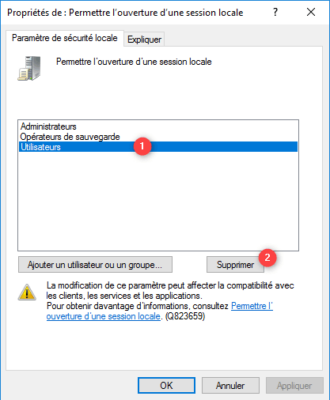
Click on Apply 1 and OK 2 to validate the parameter.
Now force the update of the group policies by opening a command prompt (cmd) in Administrator and enter the command gpupdate /force.
It is no longer possible for users to log on to the server locally.
Complements
In an Active Directory environment, it is also possible to use authentication policies to limit logon to Windows servers.
Do not remove the Domain Users object from the local Users group, doing so could block access to certain shared resources