Presentation
In this tutorial, we will see how to add rules to the Windows Firewall using Group Policy.
For information, the Windows Firewall has been implemented in the Windows operating system with service pack 2 (SP2) of Windows XP. It is now part of the system and some functionalities like DirectAccess requires that it be enabled to work.
In many organizations, system administrators tend to disable the GPO firewall to prevent application blocking.
What I propose to see in this tutorial is to create a policy that will allow all traffic on the domain profile instead of disabling the firewall.
This type of rule remains dangerous, it is advisable to allow only legitimate traffic on your network
By default, the Windows firewall passes all outgoing connections unless a blocking rule is configured. Normally only the rules of incoming traffic are to be configured (RDP, VNC …)
Configuring Group Policy (GPO)
From the Group Policy Management console, right-click at the location where the policy is to be applied and click Create GPO in this domain and link it here 1 .
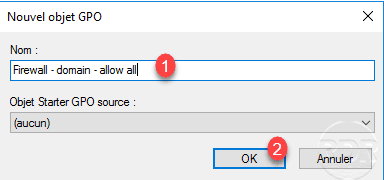
Name the strategy 1 and click OK 2.
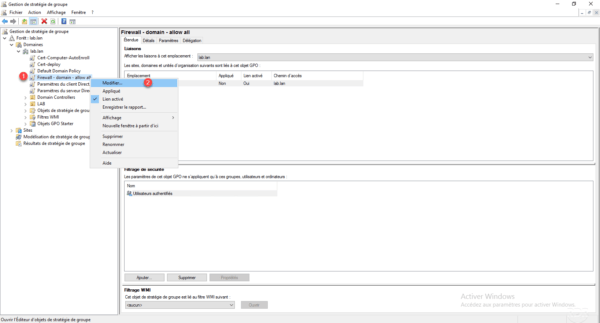
Right click on the 1 strategy and click on Edit 2 .
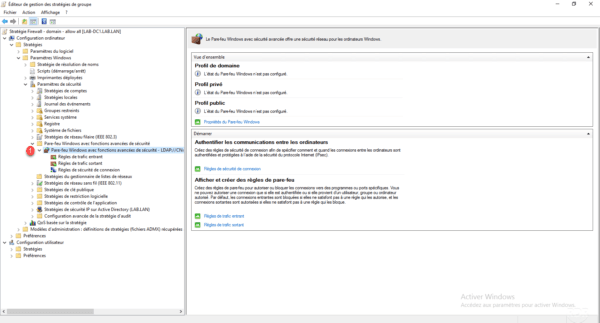
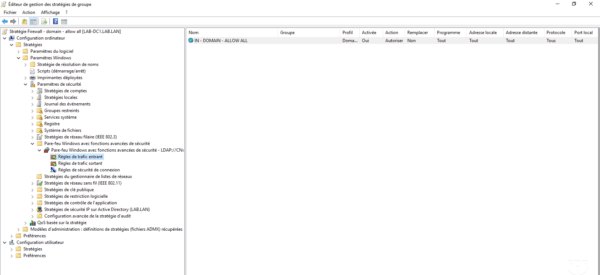
In the Group Policy Editor, go to the following location: Computer Configuration / Policies / Windows Settings / Security Settings / Windows Firewall with Advanced Security Features.
Right-click on Incoming Traffic Rule 1 then click on New rule 2 .
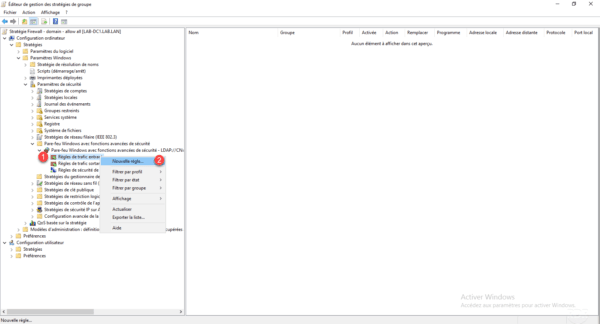
Choose the Custom rule type 1 and click Next 2 .
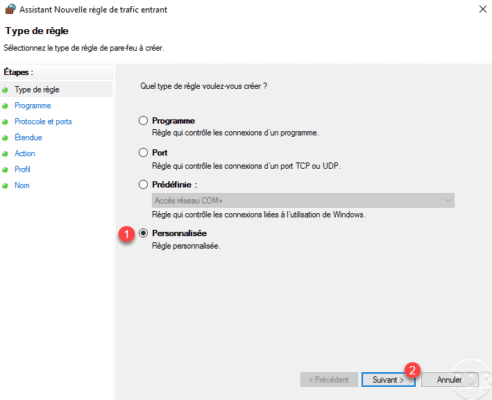
Select All Programs 1 then click Next 2 .
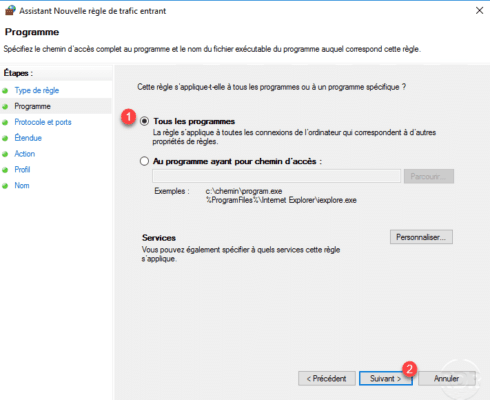
Protocol type, choose All 1 and click Next 2 .
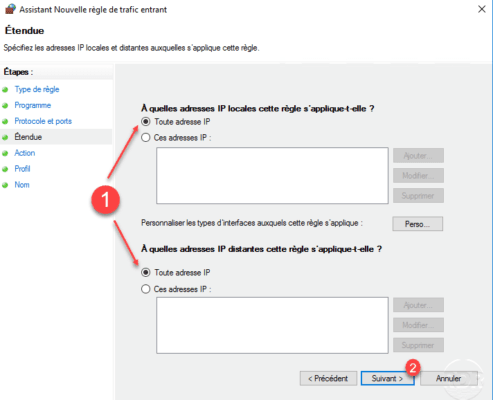
Scope configuration, choose Any IP address 1 and click Next 2 .
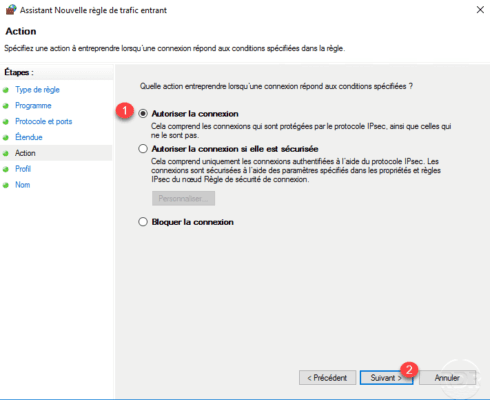
Configure the action of the rule, choose Allow connection 1 then click on Next 2 .
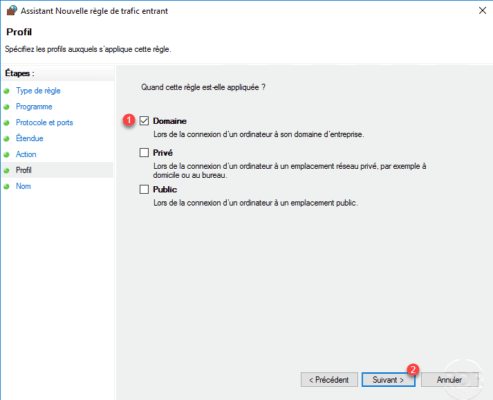
Select the profile, here to limit the risks the rule will only be applied if the computer is connected to the domain of the company, choose Domain 1 and click Next 2 .
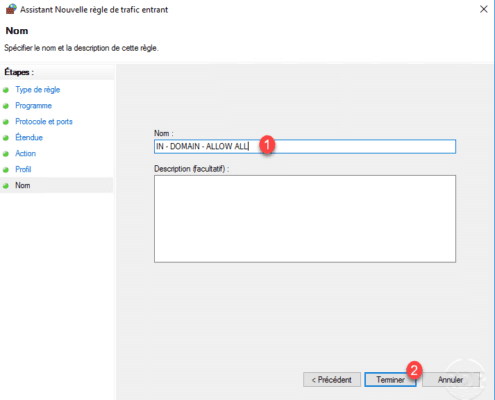
Name 1 the rule and click Finish 2 .
The rule has been added to the policy.
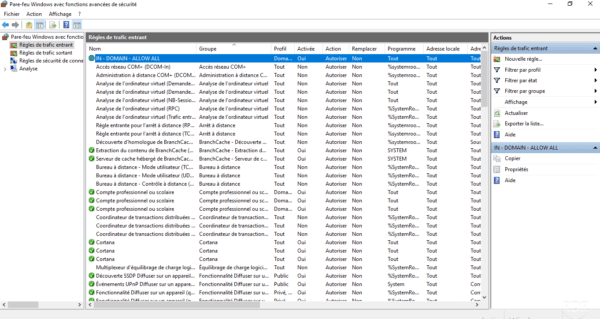
If necessary do the same for outgoing traffic. By default, outbound traffic is not blocked.
Go to a computer in the domain where the policy applies, if necessary make a gpupdate and check that the rule is present in the rules of incoming traffic.
Conclusion
In an environment where an Active Directory domain, the Windows Firewall configuration can be done by group policies and making its administration easy.
Now that you know how to create a rule, I invite you to re-enable the firewall on computers to regain control.
If a day needs to block a port on the entire park a rule in a group policy and it’s done.