Introduction
The access-based enumeration allows to display in a network share, only folders and files whose use has at least a right of reading. Other documents and folders will be hidden.
Enabling this feature will increase the CPU resource consumption on the file server because at each access this will check what should be displayed.
Enabling EBA does not hide the network share.
In order to work properly, the NTFS rights must be set correctly and requires disabling the inheritance and removing the SERVER \ Users group rights because this group contains the Domain Users group.
Enable enumeration based on access EBA
1. On the server where the share is located, launch Server Manager and go to Manage File and Storage Services and view Shares 1 .
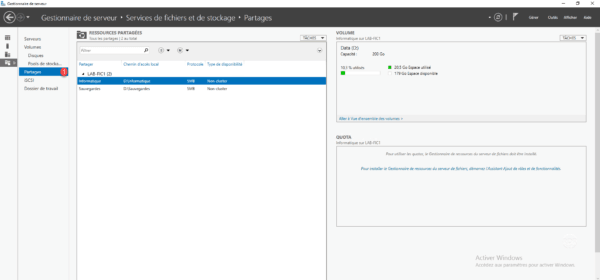
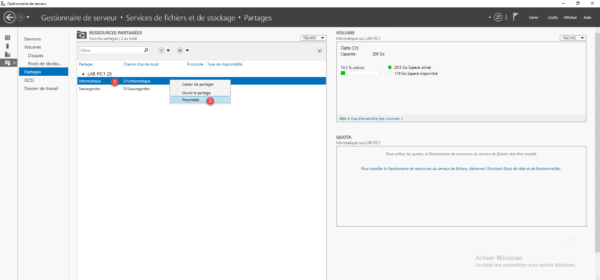
2. Right click on the shared folder 1 where the EBA must be activated and click Properties 2 .
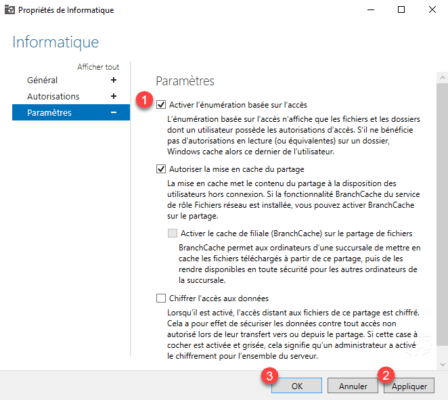
3. Check the Enable access-based enumeration 1 check box and click Apply 2 then OK 3 .
The EBA is now enabled on the shared folder, we will see now configure the rights.
Configure NTFS rights to use EBA
To illustrate the tutorial, in the IT folder, I created a folder pmartin where only the user pmartin has the rights to it.
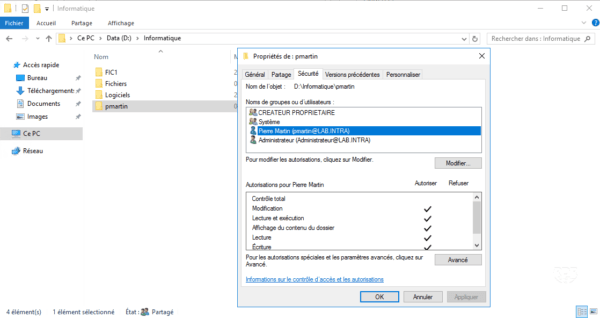
On a post, I logged in with the user dbon and I went on sharing, as can be seen on the screenshot below, the pmartin folder is not displayed.
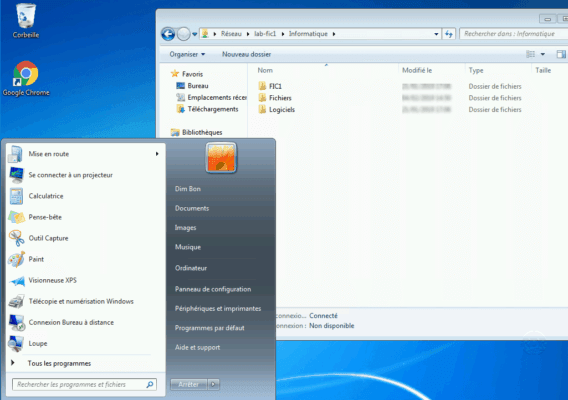
Conclusion
Access-based enumeration provides additional security by hiding folders that users do not have access to, to work properly this involves properly configuring NTFS rights.