Presentation
In this tutorial, we will see how to store the Bitlocker recovery password in the Active Directrory.
The recovery password is requested when the user forgets his pin code or when he wishes to access the hard disk on another computer when the TPM module has been used.
Viewing passwords is done using the Active Directory Users and Computers console.
Prerequisites
- Use an Active Directory environment
- The schema must be in version 40 minimum.
The schema with Windows Server 2008 is in version 44.
Configure password recording in Active Directory
Install functionality to view recovery passwords in Active Directory
In order to be able to view passwords from the Active Directory Users and Computers console, it is necessary to add functionality on one or more servers where the console is installed (generally on domain controllers).
From Server Manager, click Add Roles and Features 1.
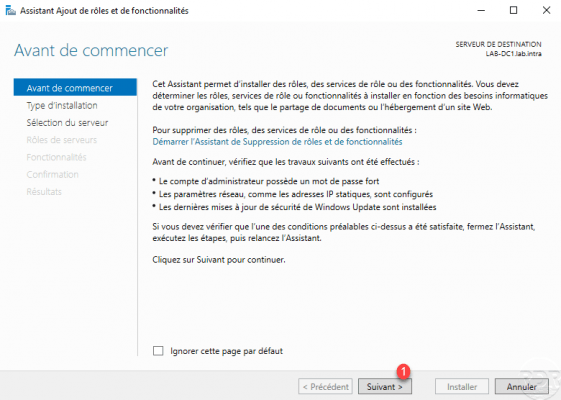
When the wizard is launched, click on Next 1.
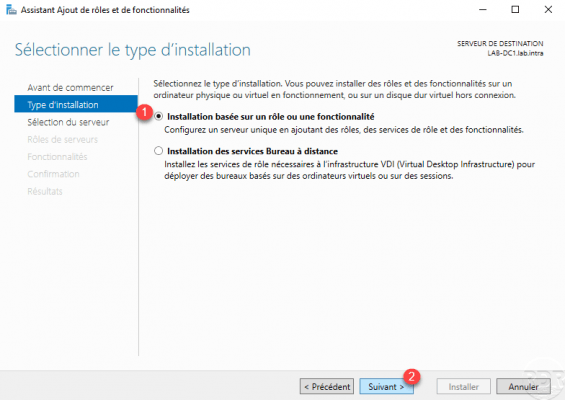
Select the Installation based on a role or a feature 1 and click on Next 2.
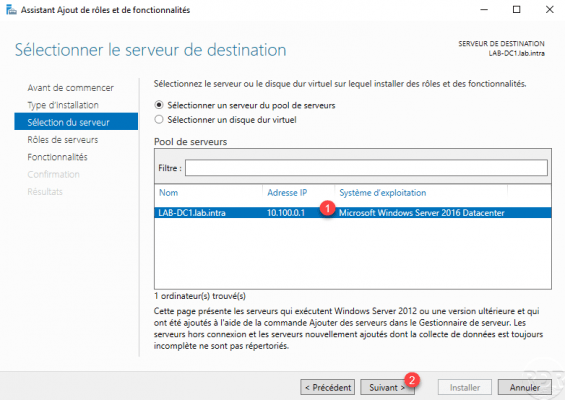
Choose the server 1 then click on Next 2.
Skip the list of roles by clicking Next 1.
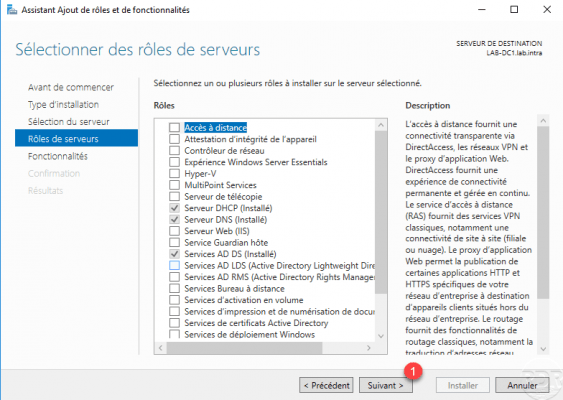
Check the Bitlocker Recovery Password Viewer 1 feature found in : Administrative Tools / Bitlocker Encryption Administration Utility. Then click on Next 2.
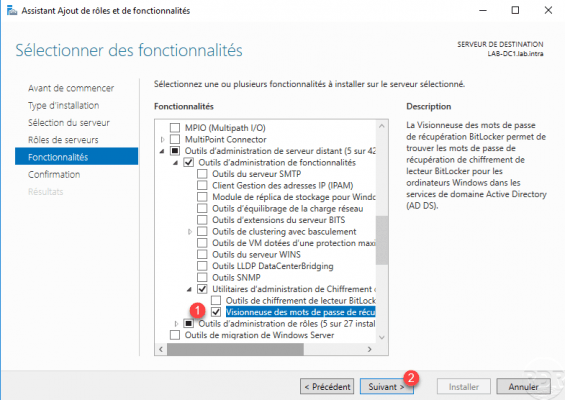
Confirm the installation by clicking on the Install 1 button.
Wait during installation …
Once the installation is complete, exit the wizard by clicking Close 1.
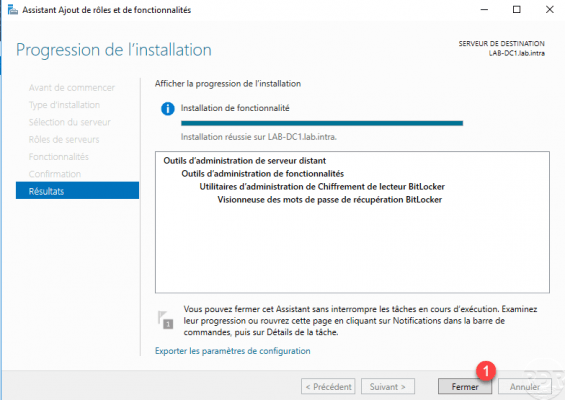
This feature adds a (Bitlocker Recovery) tab to Computer objects.
Configuring Group Policy (GPO) for Bitlocker Linking with Active Directory
In order for the Bitlocker recovery password to be saved in the Active Directory, it is necessary to configure a policy which will configure the functionality on the computer for the password stored in the AD when enabling encryption with BitLocker.
The settings that are configured in the policy can be found in Computer Configuration.
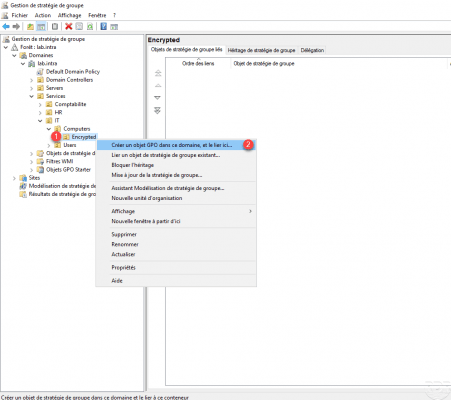
From the Group Policy Management console, click on the OU 1 where the settings must be applied and click on Create a GPO in this area, and link it here 2.
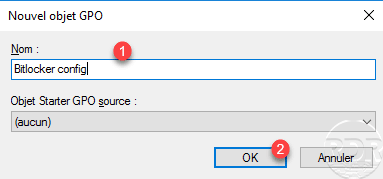
Name the group policy 1 and click OK 2.
Right click on the strategy 1 which has just been created then click on Modify 2.
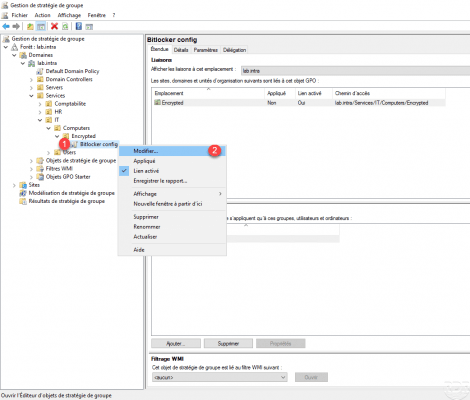
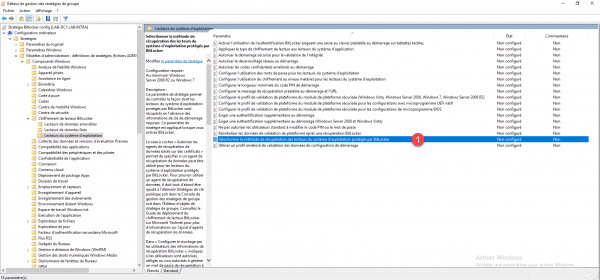
Change the setting Select the method for recovering operating system drives protected by Bitlocker 1, which is located in Computer configuration / Policies / Administrative Templates / Windows Components / BitLocker drive encryption / operating system.
Activate 1 the parameter and configure options 2 as on the screenshot and click on Apply 3 and OK 4.
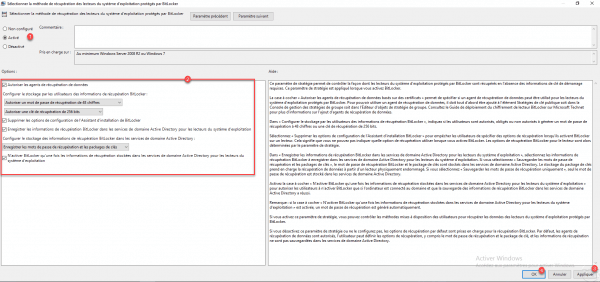
| Option | Explanation |
|---|---|
| Save BitLocker recovery information in Active Directory Domain Services for operating system drives | This option enables the recording of recovery passwords in Active Directory. |
| Remove the configuration options from the BitLocker Installation Wizard | This option removes the configuration options for activating Bitlocker. |
| Activate BitLocker only after recovery information is stored in Active Directory Domain Services for operating system drives | Cette option permet de s’assurer que le mot de passe de restauration est bien enregistré dans l’Active Directrory avant l’activation de Bitlocker. |
Close the Group Policy Editor.
Overview of strategy parameters:
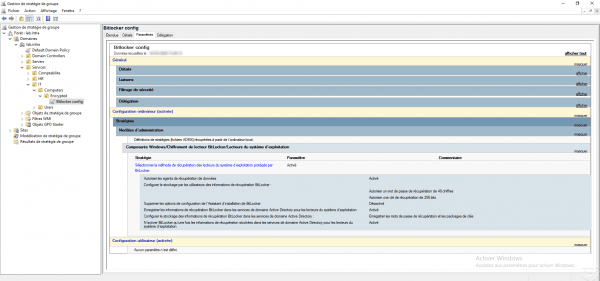
Validate the configuration
On a computer where Bitlocker is not configured, open the file explorer and right-click on the system disk 1 and click on Activate BitLocker 2.
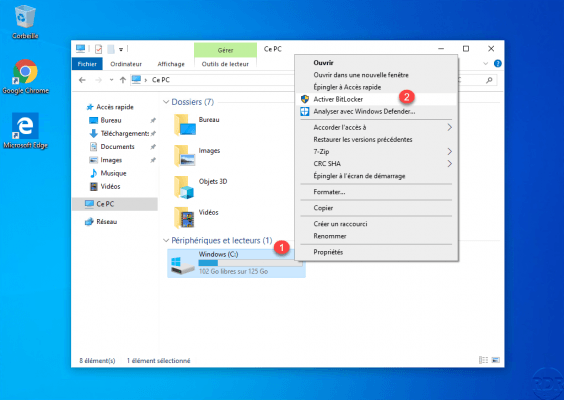
Wait while BitLocker initializes …
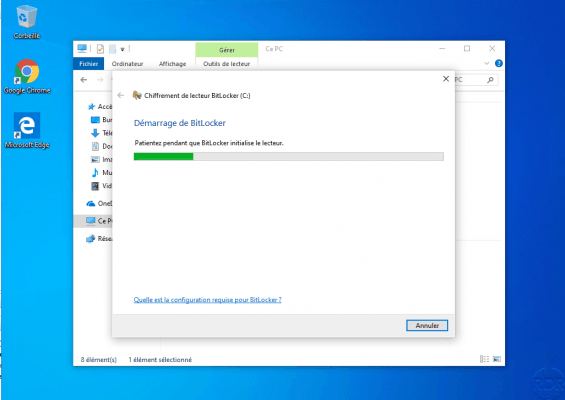
Choose how the disk space is encrypted 1 and click on Next 2.
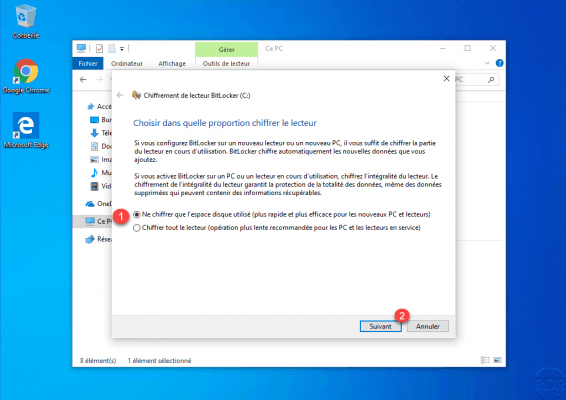
Configure the encryption mode 1 then click Next 2.
Click on Start encryption 1.
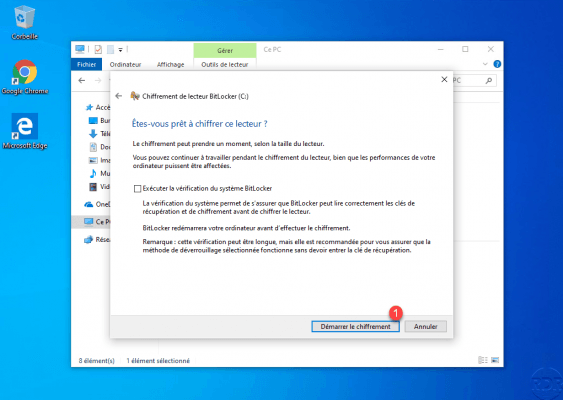
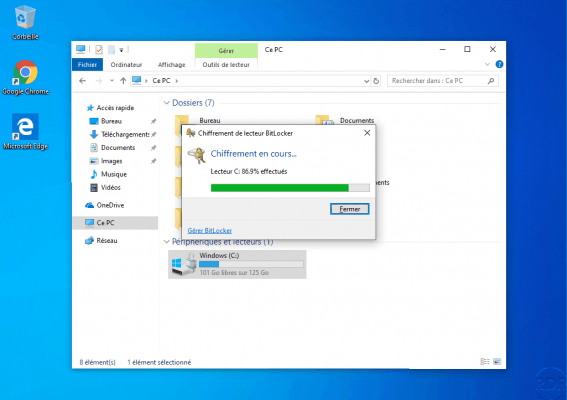
Wait during encryption …
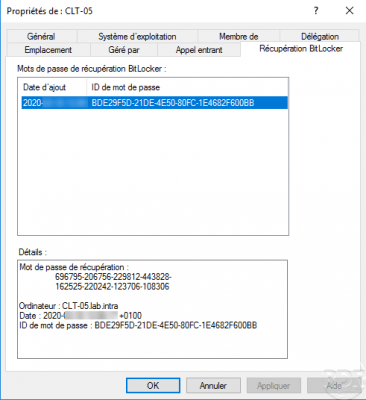
Meanwhile, go to the computer object on the Active Directory Users and Computers console, the recovery password is available on the BitLocker Recovery tab.
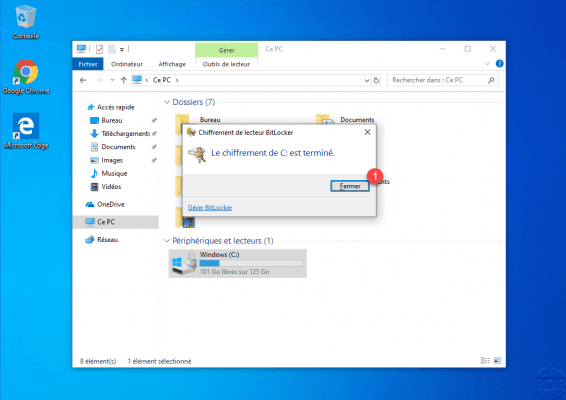
On the computer, once the encryption is complete, click on Close 1.
Conclusion
By storing recovery passwords in Active Directory, you can centralize them.