Introduction
In this tutorial, we will see how to define password policies in an Active Directory for user accounts.
By default the password policy is defined in the GPO Default Domain Policy which is applied to all computers in the domain, which makes the policy the same for all users.
Depending on the users, you may want to apply a more complex password policy for security reasons, for example members of the Domain Admins group.
For this we will use Password Settings Object (PSO) which is an Active Directory object which contains a password strategy which can be applied to one or more user groups.
Password policies are configured using the ADAC console.

Each password policy has a priority, if a user has multiple password policies that apply, the policy with the lowest priority will be applied.
To illustrate this tutorial, we will create two strategies, the first will be applied to the Domain Users group with a priority of 99 and the second will be applied to the Grp_Users_IT group which will have a priority of 98.
The policies (PSO) are stored in the Password Setting Container 1 (PSC) which is: DOMAIN / System
Password policies also manage the locking of accounts in case of bad password.
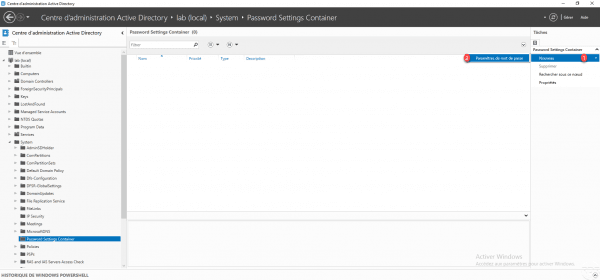
Create a password policy
From the PSC container, click on New 1 then Password settings 2.
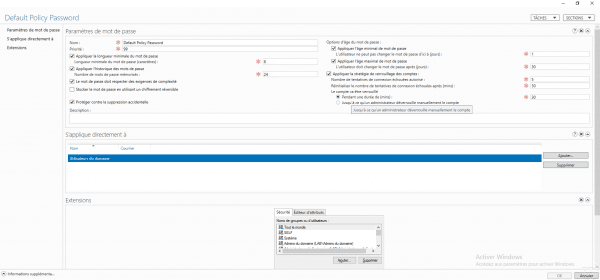
Configure the password policy settings by filling in the fields marked with an *.
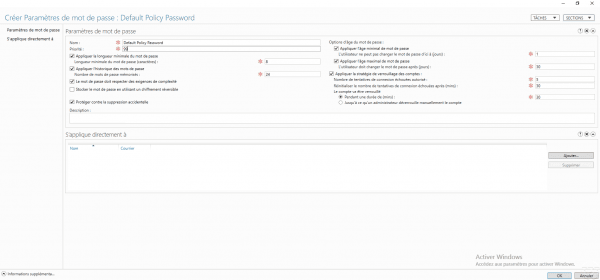
| Champ | Commentaire |
|---|---|
| Name | Password policy name |
| Priority | Weight for the application of the strategy, the lowest has priority. |
| Apply minimum password length | Minimum character length for password |
| Apply password history | Number of passwords stored that cannot be reused |
| Password must meet complexity requirements | The password must contain 3 types of characters out of the 4 available – Tiny – Capital letter – Number – Special characters |
| Apply minimum password age | Minimum password lifetime in day(s) before it can be changed again |
| Apply maximum password age | Maximum password lifetime in day(s) before expiration and change is forced |
| Apply account lockout policy | Configuration of the number of failed connection attempts and the locking time. |
Now configure to whom the script will be applied, click on Add 1.
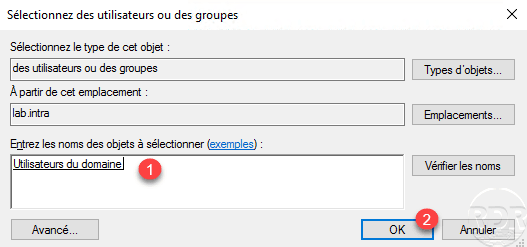
Choose the user group (s) 1 and click OK 2.
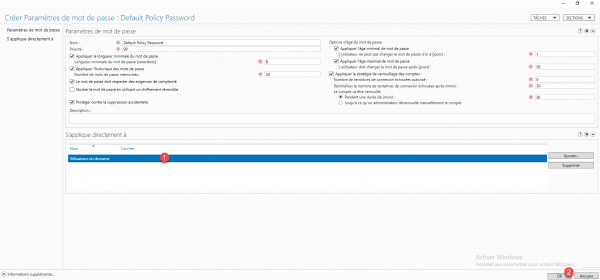
The group is added 1, click OK 2 to create the strategy.
The 1 policy is added to the container.
Create a second strategy
This part is optional, it illustrates the use of several password strategies.
Follow the same process as the first strategy, the second strategy will have a lower priority (98), a length of 10 and is applied to the Grp_Users_IT group.
In this configuration, if a user is part of the Grp_Users_IT group, the password must be 10 characters long and for other users, the password must be 7 characters long.
Identify the password strategy that applies
There are several ways to identify which policy is applied to a user or group.
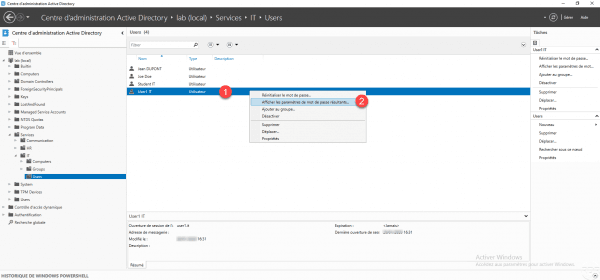
Identify a user’s password policy
Still from the ADAC console, right-click on the user 1 and click on Display the resulting password settings 2.
The password policy opens:
Identify a group password policy
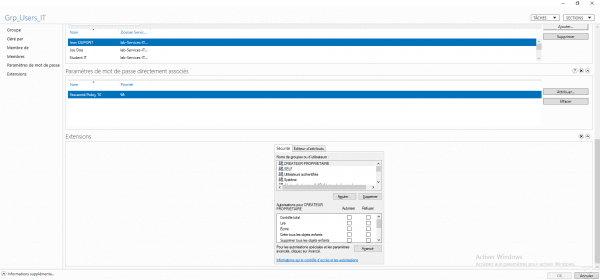
Right click on the 1 group and click on Properties 2.
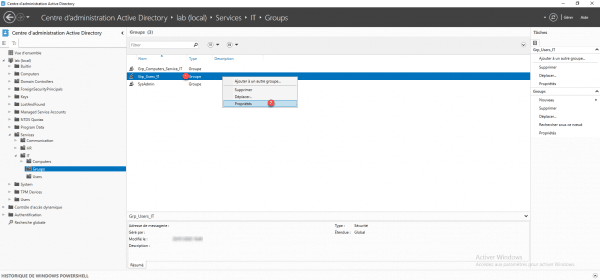
If one or more password policies apply to the group, it is displayed in the Password settings directly associated section.
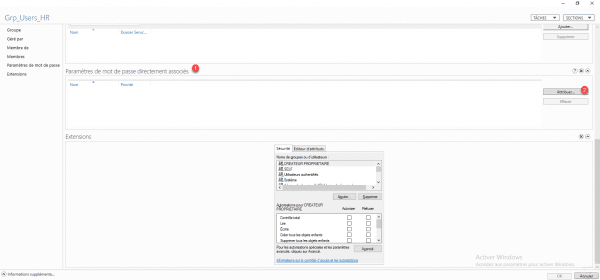
Assign an existing password policy to a group
From the properties of a group, go to the Password parameters directly associated 1 section and click on the Assign 2 button.
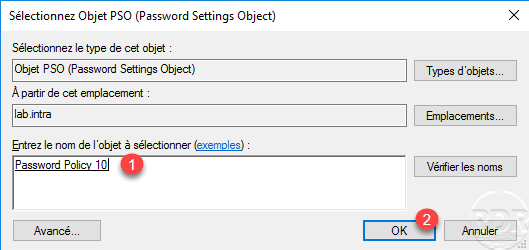
Select the PSO 1 object to assign and click OK 2.
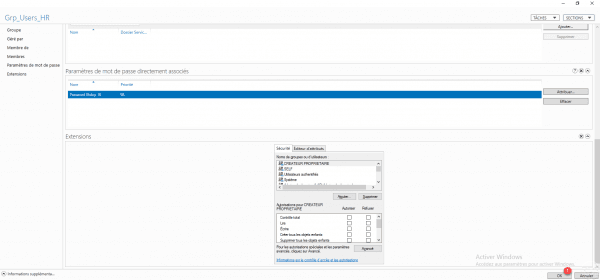
The policy is added to the group, click OK 1 to save the settings.
Test the application of the password policy
To test the application of the password policy, it is possible to create a user in the Active Directory who does not respect the conditions of the PSO.
As a reminder, the default policy defined by the GPO is 7 characters and a PSO policy which applies to all users (Domain users) was created with an 8-character requirement.
Below, a new user with a password that has 7 characters:
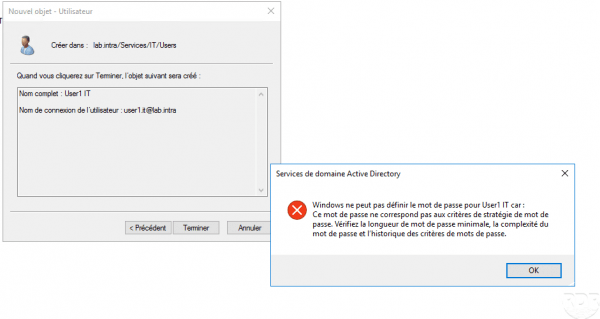
When validating the creation of the user, an error message is displayed indicating that the password does not match the criteria.
PSO password policies with PowerShell
Les PSO peuvent être administrées avec des Cmdlets PowerShell.
The command New-ADFineGrainedPasswordPolicy allows the creation of a strategy.
New-ADFineGrainedPasswordPolicy AdminsDuDomaine -ComplexityEnabled:$true -LockoutDuration:"00:45:00" -LockoutObservationWindow:"00:45:00" -LockoutThreshold:"0" -MaxPasswordAge:"24.00:00:00" -MinPasswordAge:"1.00:00:00" -MinPasswordLength:"12" -PasswordHistoryCount:"12" -Precedence:"1" -ReversibleEncryptionEnabled:$false -ProtectedFromAccidentalDeletion:$trueThe command Add-ADFineGrainedPasswordPolicySubject allows to link the strategy to a group or to a user.
Add-ADFineGrainedPasswordPolicySubject AdminsDuDomaine -Subjects "Admins du domaine"