Prerequisites and preparation for deploying AD RMS
Prerequisites for AD RMS
The deployment of AD RMS requires several prerequisites at the infrastructure level.
The most important point is the training of users in the use of this service. As we will see following this tutorial, RMS rights are applied by the creator of the document, which makes the user autonomous, unlike a traditional sharing where NTFS security is provided by the IT department.
Prerequisites for deploying AD RMS:
- An Active Directory environment.
- For the AD RMS cluster one or more servers that are members of the Active Directory domain, preferably dedicated to this role.
- In the case of a multiple AD RMS deployment, provide a minimum SQL Server 2008 database. If only one server, it is possible to use the Windows internal database (WID).
- The server (s) for AD RMS must be a member of the domain.
- Active Directory users and groups must have an email address in their attribute so that they can be used with AD RMS.
- Provide a DNS name for the AD RMS cluster:
- A recording
- An SSL certificate (Enterprise Certification Authority).
- Users must with a compatible client to be able to apply and read protected files.
- Office Pro or Adobe Pro to apply RMS rights.
- Office or Acrobat Reader to open the file (s).
Preparation of the environment
Before we start installing the AD RMS role, we will prepare the environment.
Creating a group for super users
To overcome a user error on the application of rights, it is possible to configure in AD RMS a super-admin group that has the ability to edit all files.
From the Active Directory Users and Computers console, create a group by specifying a 1 email address.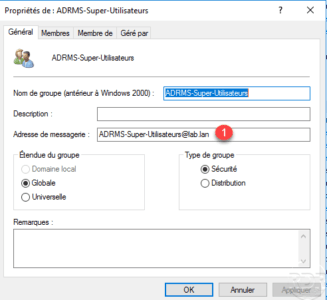
Then add the person (s) who will be able to access all the documents.
Service account for the AD RMS cluster
During post-installation configuration and the creation of the AD RMS cluster, a service account must be configured. Always using the Active Directory Users and Computers console, create a standard user account whose password never expires.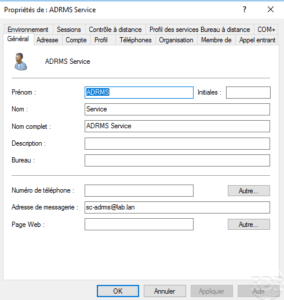
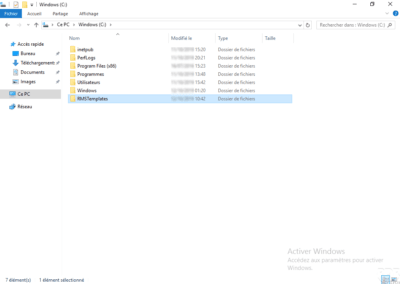
A network share
Create a network share that is readable by everyone and in total control by the service account. This sharing goes XML export service of rights strategy templates.
DNS registration
Create a DNS record for the cluster name that points to the expected server’s IP role.
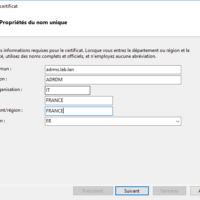
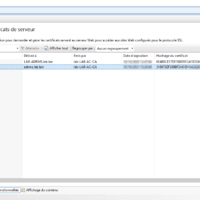
Certificate for the cluster
If you have a certification authority, provide a certificate on behalf of the AD RMS cluster.
If you do not have an IIS server to generate the certificate, you can do it from the AD RMS server after you install the roles.
SQL Server
If you want to add multiple AD RMS servers in the cluster, you need to provide a SQL Server instance